My company provides cloud storage for secure file management in small and medium-sized businesses. Since employee involvement is key in data protection, we wanted to help business professionals to understand the level of confidentiality of the information contained in standard office documents. With that goal, we created a self-assessment tool with data protection tips. More than 500 professionals at small and medium-sized businesses filled the questionnaire. Their answers revealed that two-thirds of the document types they work with have confidential content. The top three teams handling the most sensitive information are HR, executives, and legal.
HR has most confidential data
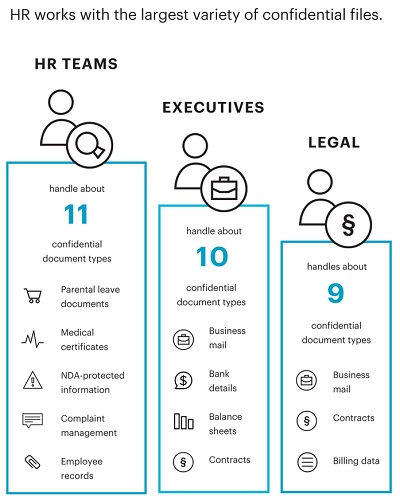 HR departments are responsible for managing documents that abound in sensitive personal data. As the questionnaire discovered, HR teams handle about 11 different confidential types, documents that contain people’s private data, or what legal experts refer to as ‘personally identifiable information’. HR not only knows more about the staff than their executives or legal teams, it also has access to the widest variety of confidential documents. HR professionals handle private data when they process job applications, oversee employee onboarding and keep track of health records, social security, salary and tax information.
HR departments are responsible for managing documents that abound in sensitive personal data. As the questionnaire discovered, HR teams handle about 11 different confidential types, documents that contain people’s private data, or what legal experts refer to as ‘personally identifiable information’. HR not only knows more about the staff than their executives or legal teams, it also has access to the widest variety of confidential documents. HR professionals handle private data when they process job applications, oversee employee onboarding and keep track of health records, social security, salary and tax information.
Damaging HR hacks
Recent examples show how harmful and expensive a breach of such data can become for staff and employers. Just a few weeks ago, Boeing spent an undisclosed amount to provide two years of identity theft protection to employees after a spreadsheet with social security numbers of 36,000 worker was emailed to a spouse by an employee asking for formatting help. Breached medical staff data, like the kind stolen in the Sony hack, can have a black-market value 10 times higher than a credit card number and may be abused for Medicare fraud.
Employees and employers trust HR teams with keeping personal information secure. Since they are the contact point for job candidates and outside recruiters, their work involves sharing confidential documents with external parties. HR departments require careful security measures to keep companies safe both from unintended employee mistakes and data breaches.
End-to-end encryption protection
SMBs are especially attractive targets for hackers because they often have limited resources for cybersecurity yet their files also contain valuable business and personal information, too. Recent studies show that more than half of the cyber-attacks target SMBs. Moreover, many reported HR hacks involved popular recruiting and payroll tools that were insufficiently secured. Small businesses need user-friendly tools that allow them to share files securely and maintain control over their data. End-to-end encryption, permissions management, and company-wide security policies help SMBs to keep ownership of confidential files.
End-to-end encryption makes company-wide file sync and sharing secure. Managing data in the cloud with end-to-end encryption means that encryption always happens on the user’s device. Files are never decrypted on the servers, which guarantees that even in the case of a server breach, hackers can only access unreadable data.
Mark Morgan, Europe Director of one of our clients, UK non-profit Stella’s Voice, says, “Encryption is an assurance to our donors that we handle information carefully. Security is paramount for us, as we share HR, financial and personal information of both our team members and the people we are helping across our sites in the UK and Moldova.”
Four steps for protecting confidential data
Protecting confidential information is a never-ending process in an organization. Companies need to conduct an analysis of threats and risks on a regular basis. They need to define priorities based on the probability of security risks and the cost of their damages. Defining what they want to protect is the first and probably hardest step to maximize confidentiality, integrity and availability without losing functionality in their IT solutions and processes.
1. Which information has value to my organization?
SMBs need to map out their data management, classify information that they need to protect, and identify the riskiest areas within their organizations.
2. What are the threats, risks and priorities?
Working with an internal or external data protection specialist can help SMBs to understand the probability of different threat scenarios and the severity of the expected consequences. Based on this, management can make educated decisions about priorities.
3. Which solutions help to mitigate those risks?
As a next step, businesses need to choose solutions for reducing risks and IT professionals can help. If there is no IT professional at hand, choosing the service complying with the respectively highest available industry norm, certification and level of encryption can be a good rule of thumb. Storing files with end-to-end encryption, managing permission levels for company files, and providing staff privacy and security training all help to safeguard confidentiality, availability and integrity of those information assets. At the same time, file backup and insurance ensure damage control.
4. How to handle changing needs?
And finally, they need to monitor the entire process and repeat these steps on a regular basis, at best annually. However, whenever a team introduces a new tool, a new risk assessment of this solution is highly recommended. After all, HR teams are the first line of defense in safeguarding the privacy of staff and job candidates.